Enhancing Docker Container Security with Anchore Grype
Written on
Chapter 1: The Rise of Container Security
With the increasing adoption of cloud technologies and container orchestration, containers have become a significant component of modern software development. Among the various container runtimes, Docker stands out as one of the most widely used. However, as this technology evolves, so does the need for robust container security, especially given the emphasis on early vulnerability detection in the development cycle.
Many organizations primarily focus on securing containers during runtime. Unfortunately, vulnerabilities can often originate at build time and remain unnoticed by those not specifically trained to identify them.
Containers are structured in layers, and most derive from third-party base images available on Docker Hub. This means that even if your application code is secure, deploying a container with a vulnerable base image can lead to serious security risks.
While system administrators typically harden operating system images for production, developers may overlook these practices due to a lack of familiarity. Traditionally, security has been the domain of SecOps professionals, who are the go-to experts for managing such concerns.
DevSecOps aims to incorporate security measures into the build and release processes, providing tools to detect vulnerabilities early in the development lifecycle. One such tool is Anchore Grype.
Section 1.1: Introducing Anchore Grype
Anchore Grype is a user-friendly container vulnerability scanner that allows you to assess your container images for vulnerabilities via a simple command-line interface. The best part is its seamless integration into CI/CD pipelines, enabling you to halt builds that exceed a predefined vulnerability threshold.
Let’s take a look at how to install Anchore Grype.
Subsection 1.1.1: Installing Anchore Grype
To install Anchore Grype, you can use the following command to download the latest installer and set up the binary in your system path:
After installation, confirm that Grype is set up correctly by running:
$ grype version
You should see a response that includes the application version and other details, confirming successful installation.
Section 1.2: Conducting a Vulnerability Scan
To scan a Docker image for vulnerabilities, execute the command:
grype <image>
For instance, to scan the NGINX image, run the command as follows:

The output will list any identified vulnerabilities along with their severity levels.
Chapter 2: Integrating Grype in a CI/CD Pipeline
To demonstrate how to utilize Grype within a CI/CD pipeline, we will use GitHub Actions. This setup will build a Docker image based on NGINX and perform a vulnerability scan before pushing the image to the container registry.
Clone the following GitHub repository for a practical example:
Within this repository, you’ll find a Dockerfile that looks like this:
FROM nginx
RUN echo 'This is a custom nginx image' > /usr/share/nginx/html/index.html
This straightforward Dockerfile creates a custom NGINX image with a simple message displayed on the homepage.
To facilitate the build process, the GitHub Actions workflow file is structured with the following steps:
- Log into Docker Hub using GitHub secrets for DOCKER_USER and DOCKER_PASSWORD.
- Build the Docker image.
- Execute a Grype vulnerability scan with a failure flag set to high. If a vulnerability of high severity is detected, the build will fail.
- If no critical vulnerabilities are found, push the Docker image to your Docker Hub repository.
To set up the GitHub secrets, navigate to your repository settings and add:
DOCKER_USER=Your DockerHub username
DOCKER_PASSWORD=Your DockerHub password
Once configured, make a change in your codebase (like editing the README file) to trigger the CI/CD pipeline. Check the Actions tab to monitor the image build process.
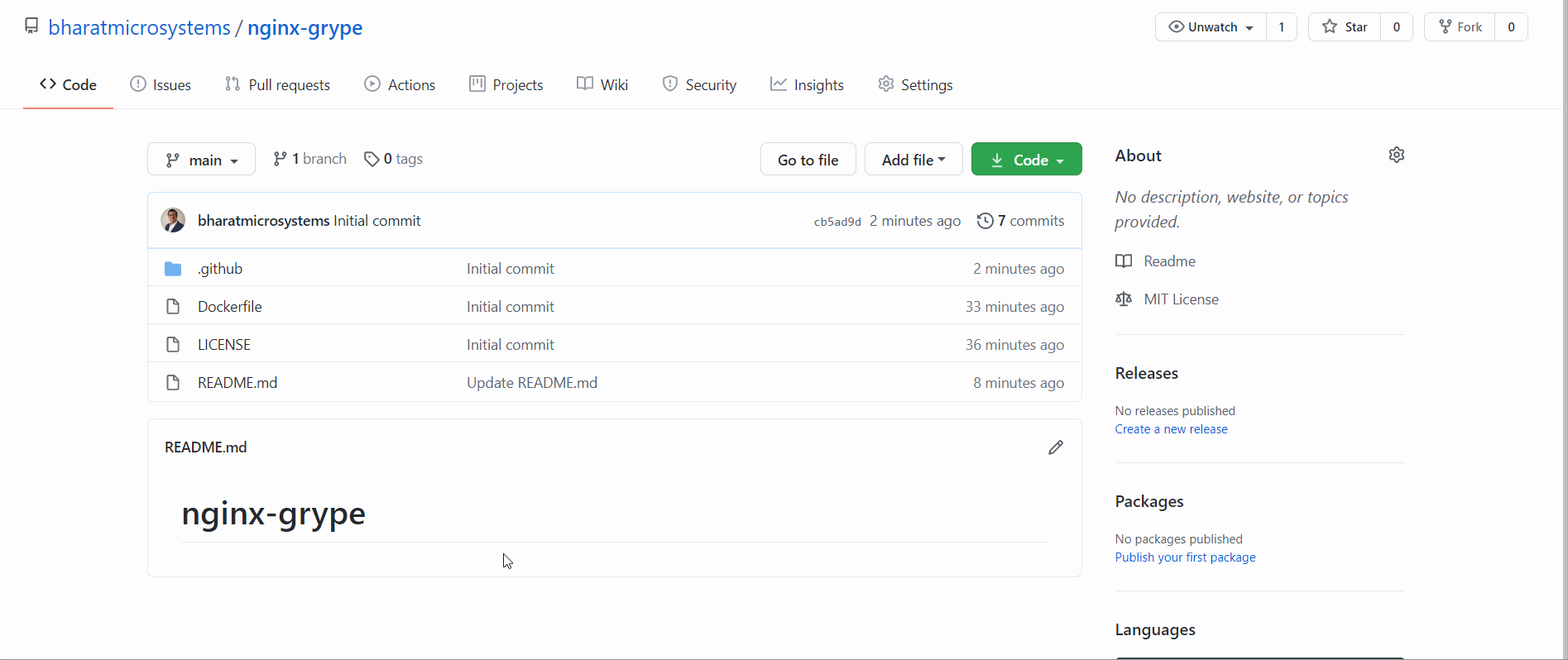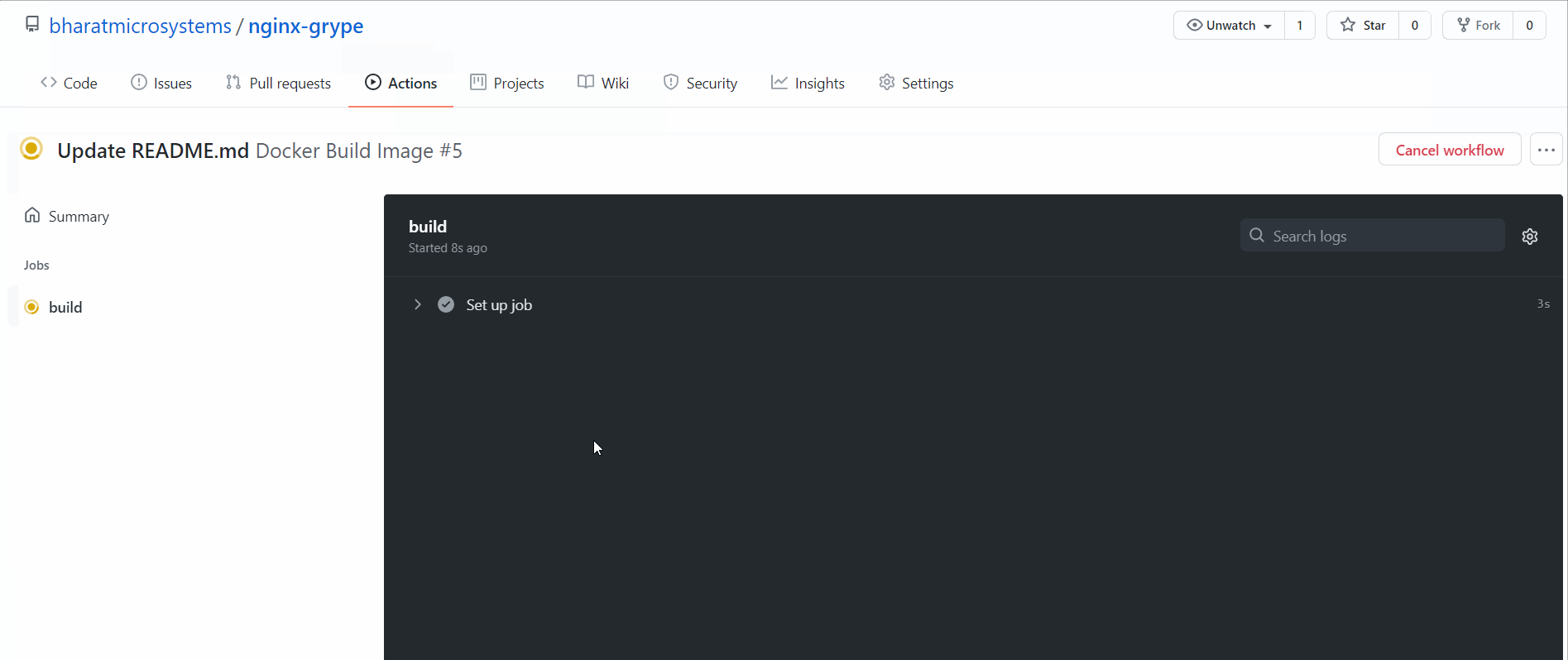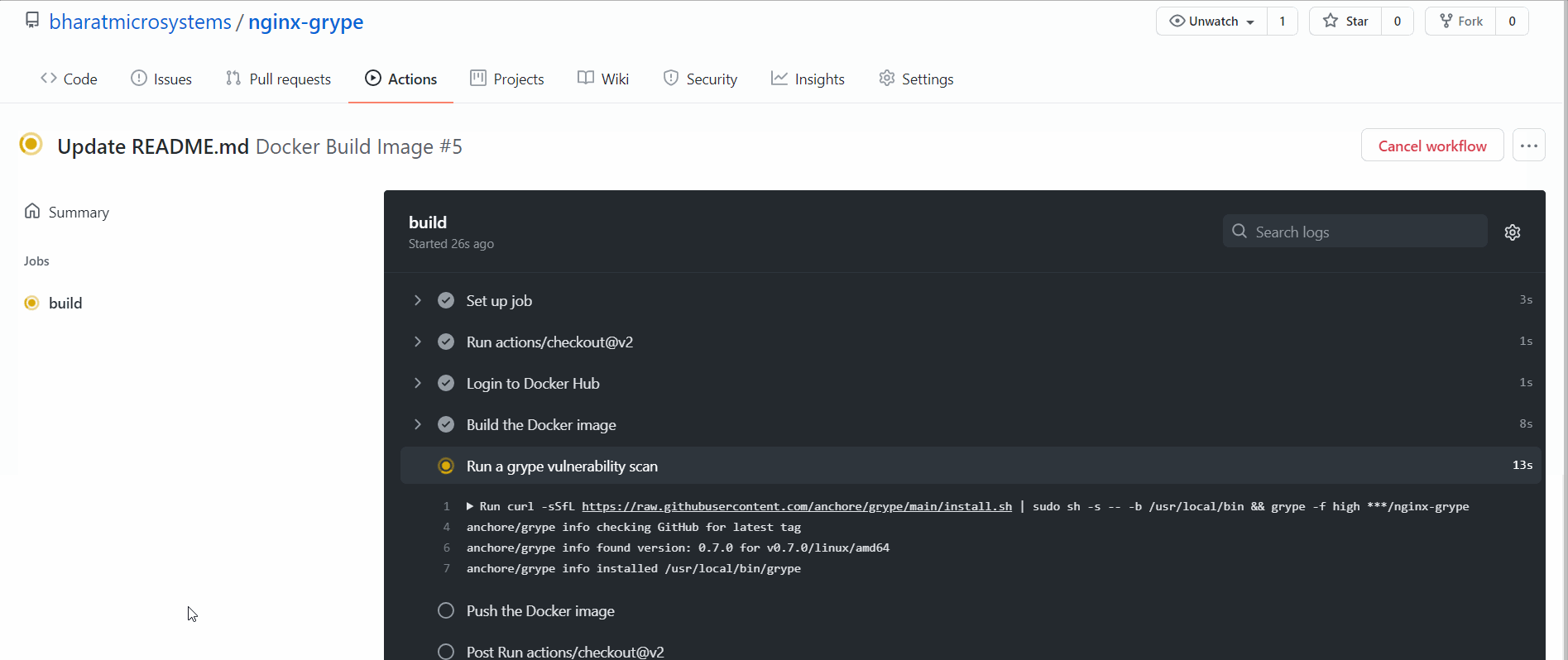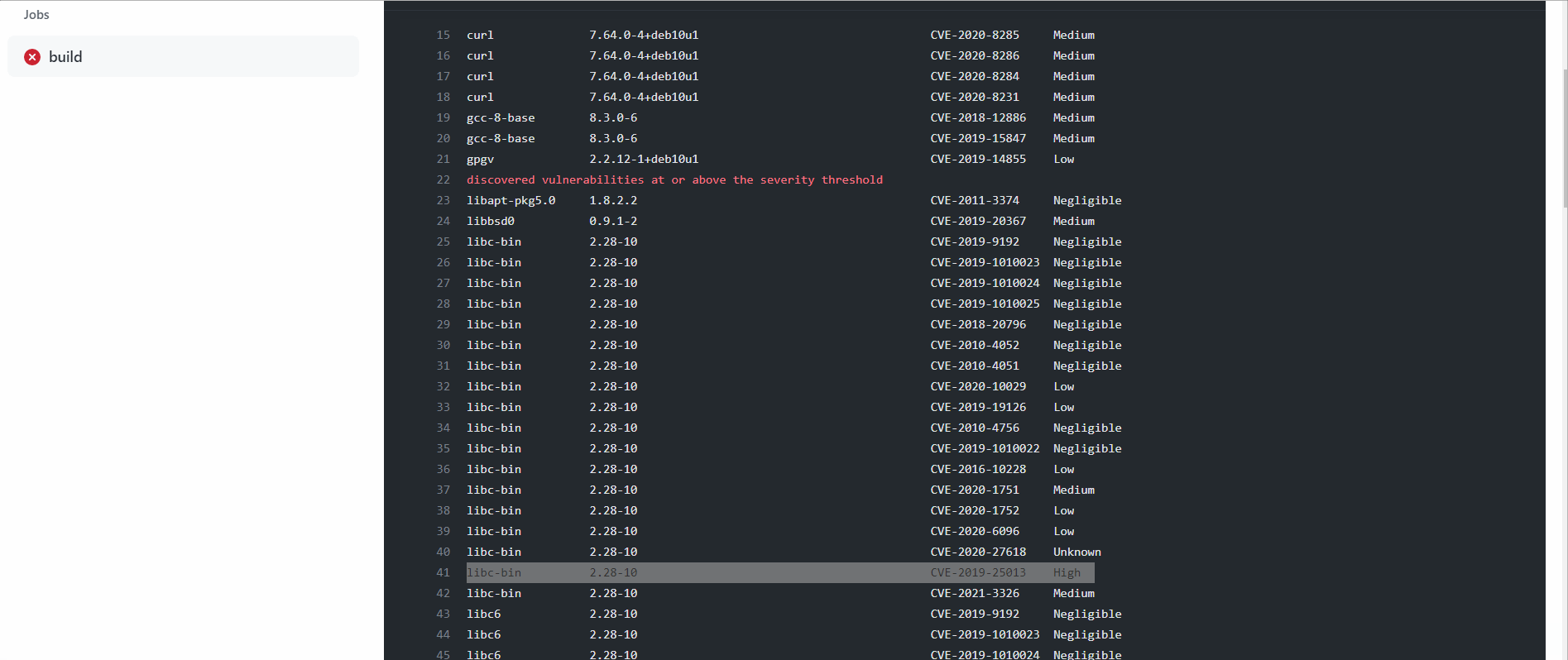
If a high-severity vulnerability is detected, the build will fail, preventing potentially harmful code from being deployed.
Conclusion
Anchore Grype serves as a robust tool for scanning container images for known vulnerabilities, supporting a variety of operating systems and language-specific packages. It plays a crucial role in ensuring that your software is built securely and remains resilient against threats.
Thank you for reading! I hope you found this guide beneficial.
Chapter 3: Video Resources
This video demonstrates how to scan Docker images for vulnerabilities using Anchore Grype, making your CI/CD pipelines more secure.
Learn how to scan Docker containers for vulnerabilities with Grype, focusing on container security in cloud environments.